From android 6.0, Google has said device manufacturers that it is mandatory to implement AES algorithm for storage encryption to ensure protection. Currently android operating system uses AES-128-CBC-ESSIV and AES-256-XTS encryption algorithms for Full-disk encryption and File based encryption which are known to be one of the fastest, robust encryption algorithms.
Unfortunetly, low-end devices today, due to AES implementation, appear to be running at low performance this is due to harware acceleration done by cryptic algorithm to encrypt the disks.
On february 5 which was Safer internet day, Google has announced a new Encryption Algorithm called Adiantum to serve encryption to android powered devices.
- [message]
- According to Google
- Adiantum is an innovation in cryptography designed to make storage encryption more efficient for devices without cryptographic acceleration, to ensure that all devices can be encrypted.
Adiantum, A special form of storage encryption algorithm built for low-end devices which include smartphones, smart watches, TV's etc. To ensure protection, it encrypts full-disk without cryptographic accelaration on hardware. It is extremly fastest encryption algorithm than AES-256-XTS. Adiantum uses ChaCha20 stream cipher to boost protection level.
The ChaCha20 stream cipher is much faster than AES when hardware acceleration is unavailable, while also being extremely secure. It is fast because it exclusively relies on operations that all CPUs natively support: additions, rotations, and XORs. said Google
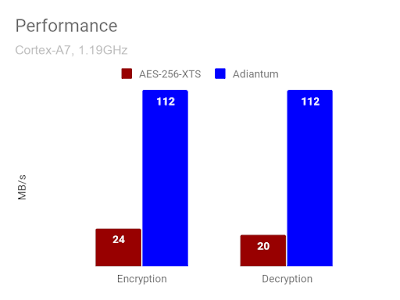
Performance of Adiantum and AES-256-XTS Algorithms when tested on ARM Cortex-A7 hardware.
Above stats say Adiantum seem to be running like charm even on low powered hardware and extremly faster than AES-256-XTS.
So, How secure is this ?
- [message]
- While talking about security, Google added that
- Cryptographic primitives like ChaCha are organized in "rounds", with each round increasing our confidence in security at a cost in speed. To make disk encryption fast enough on the widest range of devices, we've opted to use the 12-round variant of ChaCha rather than the more widely used 20-round variant. Each round vastly increases the difficulty of attack; the 7-round variant was broken in 2008, and though many papers have improved on this attack, no attack on 8 rounds is known today. This ratio of rounds used to rounds broken today is actually better for ChaCha12 than it is for AES-256.
- [message]
- Google also added
- Even though Adiantum is very new, we are in a position to have high confidence in its security. In our paper, we prove that it has good security properties, under the assumption that ChaCha12 and AES-256 are secure. This is standard practice in cryptography; from "primitives" like ChaCha and AES, we build "constructions" like XTS, GCM, or Adiantum. Very often we can offer strong arguments but not a proof that the primitives are secure, while we can prove that if the primitives are secure, the constructions we build from them are too.
So, if you are a developer want to implement this on your devices, check out this AOSP thread


![[Updated] List Of Google Dorks 2018](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiX1AKG4g7YfSAPauIO_Xro7W4Fh5zonMoNeMQkgfiPDGngH2K31hWcDTTFAe-BqB5iruO0tUyKZHU8QyJ_humO8y5Yam-BrXT7FcG7S3qxqzZeRZTViSYgGx7KY1KJITy4WSpLjrZQdO0/w680/complete+list+of+google+dorks.jpg)
Find us at